
For years, Dell customers have been on the receiving end of scam calls from people claiming to be part of the computer maker’s support team. The scammers call from a valid Dell phone number, know the customer's name and address, and use information that should be known only to Dell and the customer, including the service tag number, computer model, and serial number associated with a past purchase. Then the callers attempt to scam the customer into making a payment, installing questionable software, or taking some other potentially harmful action.
Recently, according to numerous social media posts such as this one, Dell notified an unspecified number of customers that names, physical addresses, and hardware and order information associated with previous purchases was somehow connected to an “incident involving a Dell portal, which contains a database with limited types of customer information.” The vague wording, which Dell is declining to elaborate on, appears to confirm an April 29 post by Daily Dark Web reporting the offer to sell purported personal information of 49 million people who bought Dell gear from 2017 to 2024.
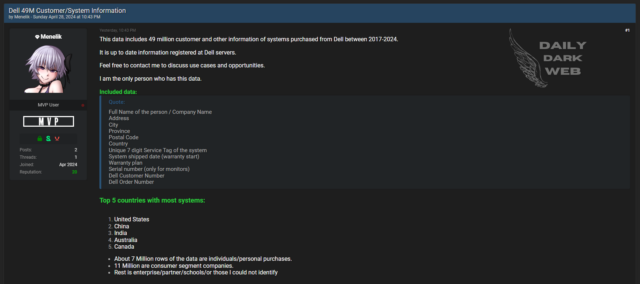
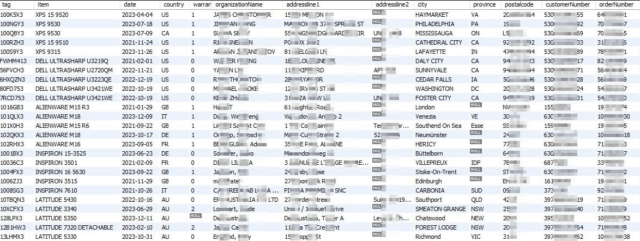
The customer information affected is identical in both the Dell notification and the for-sale ad, which was posted to, and later removed from, Breach Forums, an online bazaar for people looking to buy or sell stolen data. The customer information stolen, according to both Dell and the ad, included:
- Name
- Physical address
- Dell hardware and order information, including service tag, item description, date of order, and related warranty information
The Daily Dark Web expanded on the data the seller claimed to have acquired:
The data, claimed to be up-to-date information registered at Dell servers, includes vital personal and company information such as full names, addresses, cities, provinces, postal codes, countries, unique 7-digit service tags of systems, system shipment dates (warranty start), warranty plans, serial numbers (for monitors), Dell customer numbers, and Dell order numbers. Notably, the threat actor asserts to be the sole possessor of this data, underscoring the severity of the breach. Among the staggering number of records, approximately 7 million rows pertain to individual/personal purchases, while 11 million belong to consumer segment companies. The remaining data pertains to enterprise, partner, schools, or unidentified entities.
The “incident,” as Dell lawyers and marketers call it—or similar ones that may have occurred previously—would solve a mystery that has vexed customers and reporters for almost a decade: How are scammers obtaining information known only to Dell and the targeted customer? While neither source said phone numbers were affected, it wouldn’t be hard for scammers to use names and physical addresses to search other databases for that information.
In an email, however, a Dell representative said: “There are no indications these incidents are related,” without elaborating. The representative declined to answer any additional questions, including whether the company has any idea how customer information has been making its way into the hands of scammers for almost a decade. The notification further said: “We believe there is not a significant risk to our customers given the type of information involved.”
As I reported in 2016 and again 18 months later, scores of Dell customers have reported receiving the calls. Dell’s official response both times claimed the calls were part of an industry-wide problem that plagues many tech companies. To this day, Dell hasn’t acknowledged that the calls are different because they use information known only to Dell and the customer.People who receive unsolicited calls claiming to come from Dell should hang up and either ignore them or call the Dell support line directly. They shouldn’t engage with the caller or provide any information. It’s also possible that scammers in possession of this information could use it in mail sent to their email or physical address, assuming the scammers can find it through a people search service. The same advice applies.
Promoted Comments