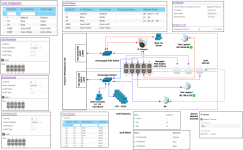
I just bought a GS110TPv3 with the intention of setting up VLANs to eventually segregate WiFi traffic from a common UniFi WAP, but first I wanted to test with just a plain ol' laptop and Ethernet cables, to be sure I understand how to set up the VLANs. Well, I don't, despite I've watched this video several times and read this page and this page as well.
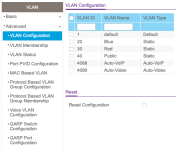
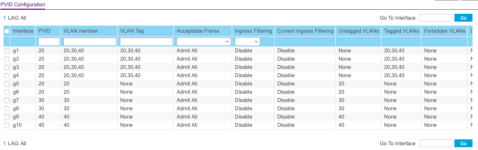
I defined VLAN20 and assigned it to ports 2 and 7 on the switch as Untagged, as I think I want these to be access ports, right?
I defined VLAN30 and assigned it to ports 3 and 8 on the switch as Untagged.
VLAN1 is the default/native VLAN, Untagged on all ports by default, so I removed it from 2,3,7, and 8.
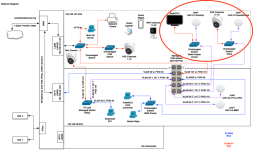
I started out with a simple test, connecting switch Port 1 to my LAN0, and connecting my laptop to Port 5. I get a connection and a DHCP address of 0.233, which the same as if I'd connected my laptop directly to the blue switch. This also works on port 4 or 6.

Then I connected the cables like this, thinking that Ports 2 and 7 would behave like a switch, and connect me to the blue network, but I get a Not Connected:

a similar test through ports 3 and 8 fails:

If I connect directly from my laptop to the red switch, I get a .50.x DHCP address"

So I must have entered something incorrectly or neglected to turn something on. Anyone know Netgear managed switches?
Thanks!
I defined VLAN20 and assigned it to ports 2 and 7 on the switch as Untagged, as I think I want these to be access ports, right?
I defined VLAN30 and assigned it to ports 3 and 8 on the switch as Untagged.
VLAN1 is the default/native VLAN, Untagged on all ports by default, so I removed it from 2,3,7, and 8.
I started out with a simple test, connecting switch Port 1 to my LAN0, and connecting my laptop to Port 5. I get a connection and a DHCP address of 0.233, which the same as if I'd connected my laptop directly to the blue switch. This also works on port 4 or 6.

Then I connected the cables like this, thinking that Ports 2 and 7 would behave like a switch, and connect me to the blue network, but I get a Not Connected:

a similar test through ports 3 and 8 fails:

If I connect directly from my laptop to the red switch, I get a .50.x DHCP address"

So I must have entered something incorrectly or neglected to turn something on. Anyone know Netgear managed switches?
Thanks!